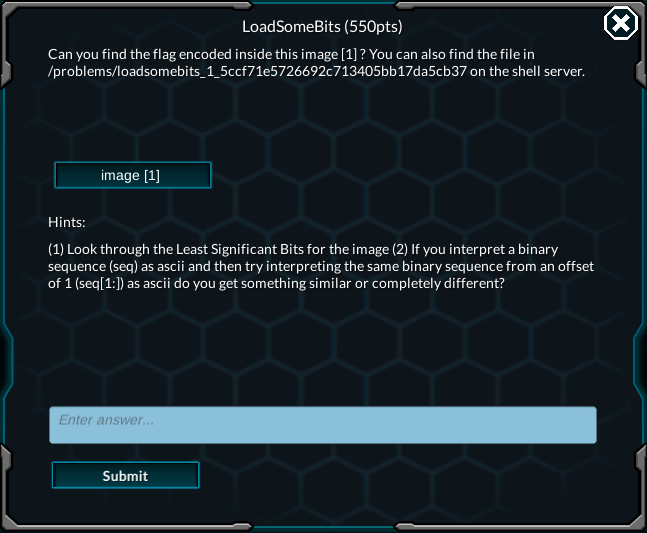
題目: LoadSomeBits
圖片下載下來看起來就是很普通圖片
加減還是分析一下
root@hackercat:~/CTF/picoCTF2018/Forensics/LoadSomeBits# file pico2018-special-logo.bmp
pico2018-special-logo.bmp: PC bitmap, Windows 98/2000 and newer format, 1200 x 630 x 24想說用StegSolve分析看看 結果出現error
看了一下bmp的magic number是42 4D沒有錯
仔細再看看hint
(1) Look through the Least Significant Bits for the image
(2) If you interpret a binary sequence (seq) as ascii and then try interpreting the same binary sequence from an offset of 1 (seq[1:]) as ascii do you get something similar or completely different?突然看到題目想起來?! 難道是LSB
LSB隱寫
:::success
文件是由bytes組成 每個byte是8bits
譬如 10101100 (最後一個0就被稱為LSB)
1st digit is MSB and Last digit is LSB
改變LSB(最低有效位元)並不能使值發生很大的變化
譬如
10101100 (base 2)== 172 (base 10)
將LSB改成1
10101101 (base 2)== 173 (base 10)
:::
不過看懂原理了其實還是不知道怎麼實作 = =”
:::warning
Python位運算符:
位運算符作用於位和位操作執行位。
假設,如果a =60;且b =13;現在以二進製格式它們將如下:
a = 0011 1100
b = 0000 1101
(a & b) = 12 即 0000 1100
也就是只有遇到1跟1才會留下1
其他都是0
:::
寫個程式
把每個bytes的最低位元取出來
import binascii
import time
data = open('pico2018-special-logo.bmp','rb').read()
s = ''
for d in data:
# print('d: ',d)
# print('ord(d): ', ord(d))
# print('str(ord(d)): ', str(ord(d)))
s += str((ord(d)) & 1)
# time.sleep(3)
# print(s)
for it in range(16):
ss = ''
try:
ss = binascii.unhexlify('%x' % int(s[:-it], 2))
except:
pass
if 'pico' in ss:
print ss[ss.find('pico') : ss.find('pico') + 60]
break得到flag
picoCTF{st0r3d_iN_tH3_l345t_s1gn1f1c4nT_b1t5_882756901}
上面程式目前還是搞不懂為什麼要offset range(16)
工具整理
工具
eog,feh (terminal下開啟圖片,這兩個都可以用apt安裝)
file (簡單查看檔案資訊,檔案類型)
exiftool (apt安裝)
binwalk
foremost
fdisk
fsck
testdisk
zsteg (github資源)
xxd, hexedit, bvi (hex模式)
Stegsolve(GUI介面的,用java寫的)
StegDetect(針對jpg windows的)
Stegosuite(也是用java寫的)(https://stegosuite.org/)
各式各樣的hex editor
https://www.ubuntupit.com/best-linux-hex-editor-top-20-linux-hex-viewers-editors/